Proposed protocol simulation in presence of the intruder.
4.9 (222) · € 20.50 · En Stock

Electronics, Free Full-Text

Computers, Free Full-Text

Secure intrusion detection system routing protocol for mobile ad
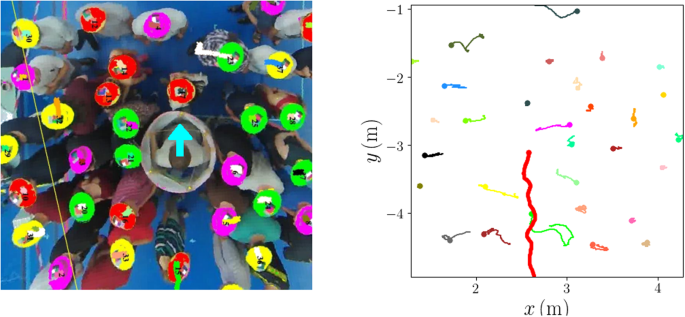
Mechanical response of dense pedestrian crowds to the crossing of
Proposed protocol simulation in presence of the intruder

The Needham Schroeder Public Key protocol simulation.

An accurate attack detection framework based on exponential

Secure intrusion detection system routing protocol for mobile ad
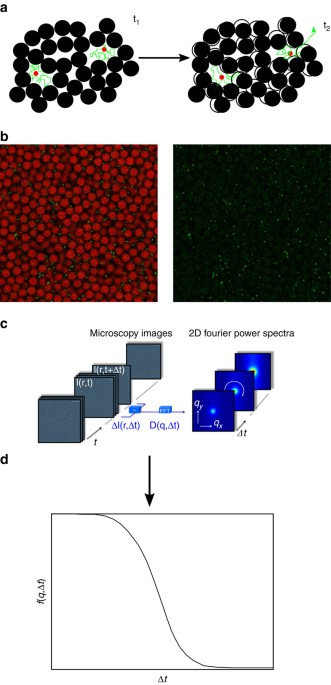
Anomalous dynamics of intruders in a crowded environment of mobile

Introduction into SkyRadar's Breach, Attack and Defense Simulator

Modeling and verifying NDN‐based IoV using CSP - Chen - 2022

Basic animation with the intruder, the intruder may take advantage

Enhancing the Elliptic Curve Integrated Encryption Scheme in 5G

Analysing Security Protocols Using Scenario Based Simulation

A novel authentication protocol to ensure confidentiality among











